Hello there! In this blog, we will discuss what are APIs, how they work, types of APIs, APIs methods and most importantly how to keep them safe. So, let's dive into it.
What is API?
API is the acronym for Application Programming Interface.
It is a set of commands, functions, protocols and objects.
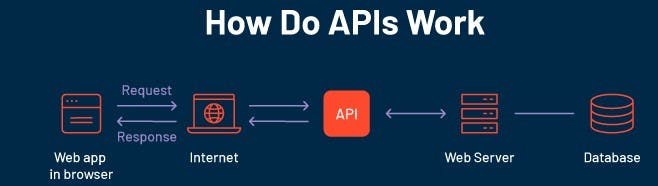
It is a software interface that allows two applications to interact with each other without any user intervention.
Each time you use an app like Instagram, send an instant message or check the weather on your phone, you're using an API.
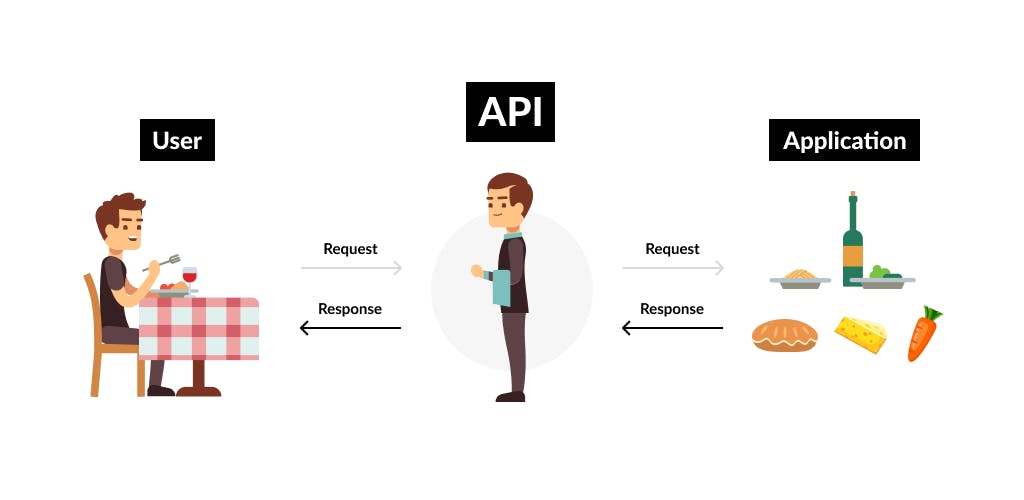
Real Life Example
Imagine you’re sitting at a table in a restaurant with a menu of choices to order from. The kitchen is part of the system that will prepare your order. What is missing is the critical link to communicate your order to the kitchen and deliver your food back to your table. That’s where the waiter or API comes in. The waiter is the messenger or API that takes your request or order and tells the kitchen (the system) what to do. Then the waiter/API delivers the response back to you so that you can pick up your order; in this case, it is the food.
Types of APIs
There are mainly 2 types of APIs that are used widely:

1. SOAP API
SOAP stands for Simple Object Access Protocol.
SOAP APIs use the SOAP protocol, which is a messaging protocol for accessing web services over HTTP.
It transports data in standard XML format.
It is very secure.
Caching is not possible.
However, it works slower and is heavier.
2. REST API
REST stands for Representational State Transfer.
It relies on HTTP (Hypertext Transfer Protocol).
It transports data in JSON format.
It is less secure.
Caching is possible.
It is faster and lighter.
This is commonly used in web services.
Anatomy of an API
An API consists of the following:
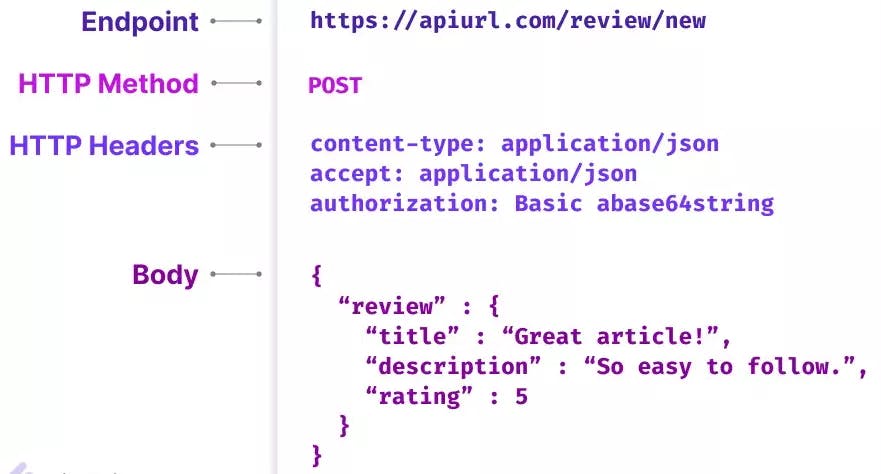
Endpoint- It contains a Uniform Resource Identifier (URI) indicating where and how to find the resource on the Internet. It is the touchpoint where the API and the client connect and communicate.
Header- It stores information relevant to both the client and server. Mainly, headers provide authentication data such as an API key, the name or IP address of the computer where the server is installed, and information about the response format.
Body- It is used to convey additional information to the server. This option is only used with
POST,PUT,PATCHorDELETErequests.Method- It defines the kind of method request and method response. Some of the methods are
GET,POST,PUT,PATCHandDELETE.Parameters- These are user specifications passed to the endpoint that affects the type of response generated. These are added after a ? in the URL.
Status Codes- It refers to a code number in the response header that indicates the general classification of the response.
API Methods
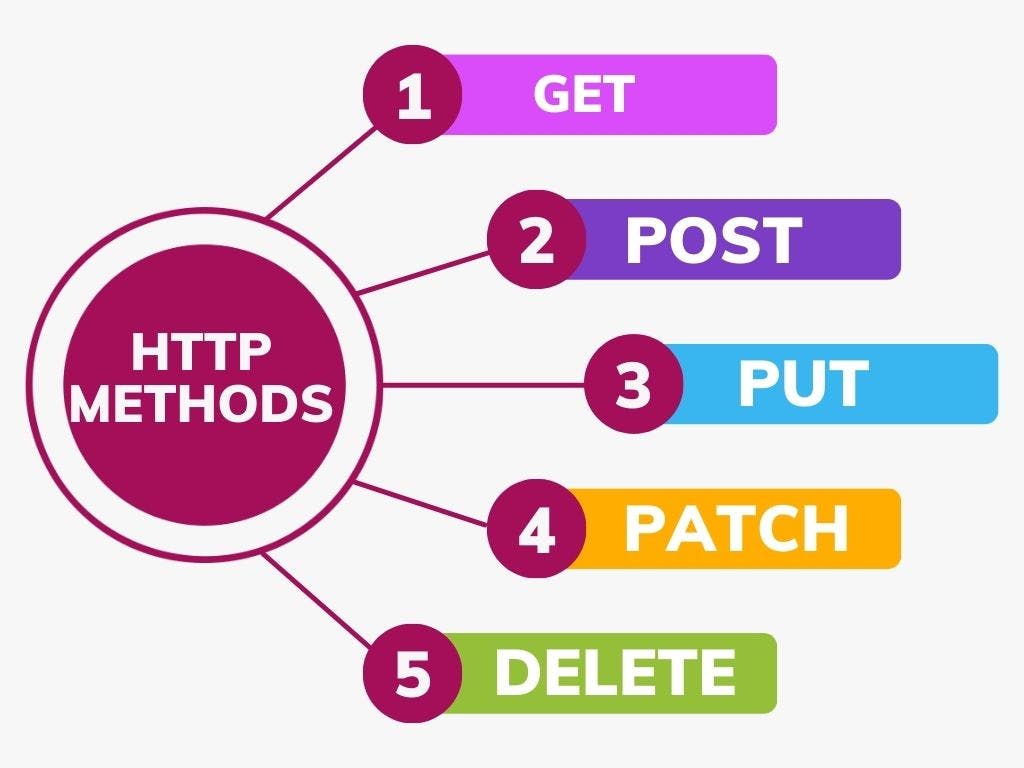
GET- This request is used to get a resource from a server. If you perform a
GETrequest, the server looks for the data you requested and sends it back to you.POST- This request is used to create a new resource on a server. If you perform a
POSTrequest, the server creates a new entry in the database and tells you whether the creation is successful.PUT- If you perform a
PUTrequest, it will replace or overwrite the data if data is already present in the database.PATCH- If you perform a
PATCHrequest, the server updates an entry in the database and tells you whether the update is successful.DELETE- This request is used to delete a resource from a server. If you perform a
DELETErequest, the server deletes an entry in the database and tells you whether the deletion is successful.
Status Codes

Informational Responses (1XX)- It means the request has been received and the process is continuing.
Success Responses (2XX)- It means the action was successfully received, understood, and accepted.
Redirection (3XX)- It means further action must be taken to complete the request.
Client Error (4XX)- It means the request contains incorrect syntax or cannot be fulfilled.
Server Error (5XX)- It means the server failed to fulfill a valid request.
How APIs are made?
APIs are made on the backend by specifying the following things:
Routes- Routes direct incoming API requests to backend resources. It defines the path for hitting the exact data point.
Controllers- A controller is a class that implements operations defined by the application's API. It consists of functions.
Models- A model is an object that represents the data in the API. It specifies the schema of data.
API Security Methods
API security is the process of protecting APIs from attacks. Because APIs are very commonly used, and because they enable access to sensitive software functions and data, they are becoming a primary target for attackers.
HTTPS- Using HTTPS instead of HTTP ensures the security of the APIs. HTTP is secure because it uses an encryption protocol known as Secure Sockets Layer (SSL)/Transport Layer Security (TLS).
Password Hashing- Hashing turns your password (or any other piece of data) into a short string of letters and/or numbers using an encryption algorithm. If a website is hacked, cybercriminals don't get access to your password. Instead, they just get access to the encrypted “hash” created by your password.
Not keeping sensitive information in URL- Be careful not to accidentally expose your API key in the parameter of the URL This also applies to any passwords, usernames, and session tokens.
OAuth- Open Authorization is an authorization protocol that gives an API client limited access to user data on a web server. It enables apps to obtain limited access (scopes) to a user's data without giving away a user's password.
Timestamp- By including a timestamp in the request headers, the server will have control over whether the request was sent promptly or not.
That's it for this blog on APIs. We use APIs on a daily basis and we must have information about this. If you have any queries, then feel free to drop them in the comment box. I'd be glad to address your queries. Until then, bye bye and take care!